Use Group Policy to enforce 2-factor on Windows servers/workstations


The most flexible way to enforce 2-factor authentication is to use Windows' built-in security controls. Our User Group Pairs feature means that you can set up group policies and ACLs that are aware of AuthLite Users and whether they logged in with two factors.
Important: The following is one of the most critical concepts to understand in AuthLite
In order to be Enforced as 2-factor, a user must be both an AuthLite User and requesting access to a computer or resource that has been told to enforce 2-factor for AuthLite Users. See (Fig. 1) for an illustration. This has important implications:
- Simply being an AuthLite User alone is not enough to "enforce" anything. You also have to tell the resources that they should be enforcing 2-factor for AuthLite Users. And conversely:
- Simply telling a resource to enforce 2-factor for AuthLite Users will not block other, non-AuthLite Users from authenticating. This is very important to understand. You still can block whatever users and groups that you want, but you just use your existing group policy and ACL controls to do that; it has nothing to do with AuthLite.
AuthLite does not replace existing permission controls (AuthLite does not try to block non-AuthLite users). AuthLite just adds one more "check": if you're an AuthLite user and you are logging onto something that blocks access from 1-factor AuthLite users then enforcement occurs.
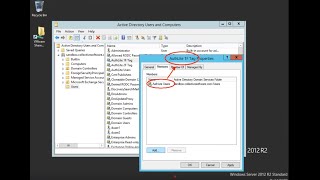
You can use Group Policy to restrict how AuthLite Users are allowed to authenticate to certain machines, by setting the "Allow" (green highlight) and "Deny" (red highlight) sections in "User Rights Assignment", as shown in Fig. 2. Please refer to the video for a walkthrough of this feature.
Note: Make sure to test that 1-factor authentication is blocked as you expect. It is possible in AuthLite to have 2-factor working but without properly enforcing 1-factor yet.
